With a WiseMo solution, you have strong authentication features available to protect against un-authorized access to your computers and devices. Managed centrally, or defined on the end-point.
myCloud Device Access Control (mDAC)
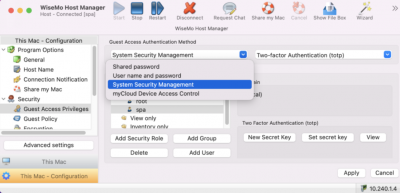
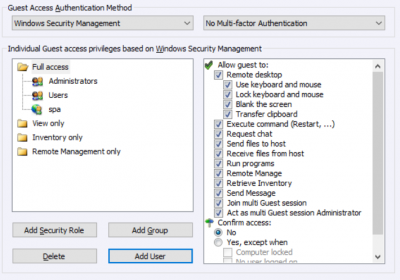
Central management of authentication and authorization. Which users may access which computers and devices – and if authenticated for remote access, what are such user permitted to do on the remote computer / device. Easy to add users for remote access, easy to remove users from access. Easy to add or remove a target computer or device. Easy to define or change what a certain user is permitted to do on a specific device.
System authentication
A remote user trying to access a computer can be authenticated via integration to this computer’s system authentication. For Windows PCs and Windows Servers, authenticate via Windows computer or domain authentication (e.g. using Active Directory). For Mac computers, authenticate via integration to macOS System security. For mobile devices, consider using WiseMo user authentication or mDAC.
When using system authentication, access to the computer is granted to system users or to system groups. This means that access to a computer can be controlled centrally by administering system users and their membership of system groups.
WiseMo user authentication
If system authentication is not relevant, use one of the other authentication options available on the end-point (the Host), including the possibility to define your own choice of user name and password, often used for Mobile devices, e.g. Android or Windows Compact Embedded devices. Or protect access with just a password, if ease of use is more desirable than the strongest access protection – for example if it is only you that need to access a computer on your internal LAN.
Two-factor authentication
Furthermore, when access control is handled by the individual Host, you can also protect the end-point computer / device with an extra layer of security by enabling two-factor authentication, where a constantly changing verification code must be entered to gain access. The verification code is for example generated by the Google authenticator app, or Microsoft authenticator app, on a Smartphone (the second factor). Very secure for your most critical computers – ATMs, Servers and your home computer.
Two-factor authentication can also protect a myCloud User account, making the use of mDAC for central security management even more secure.